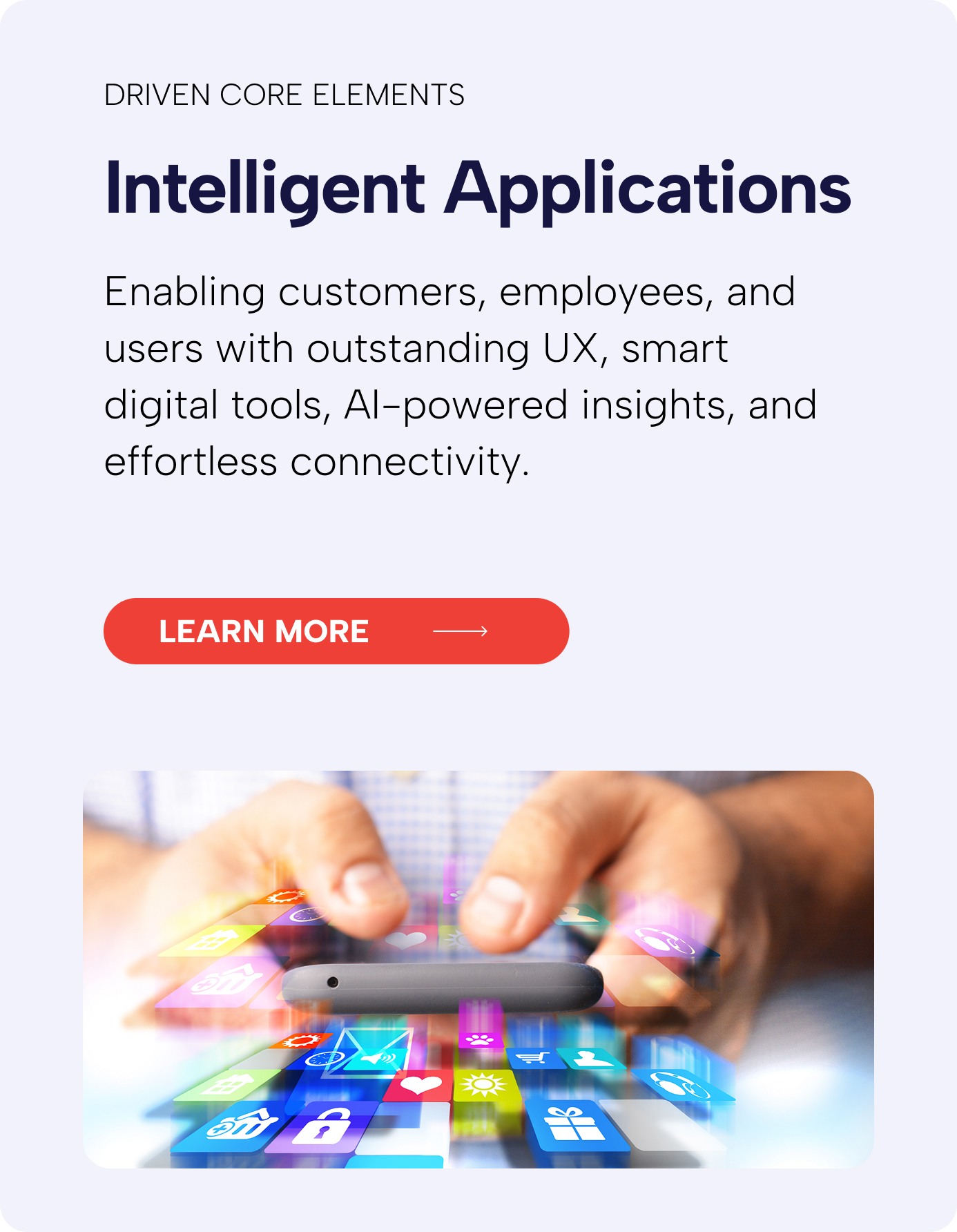
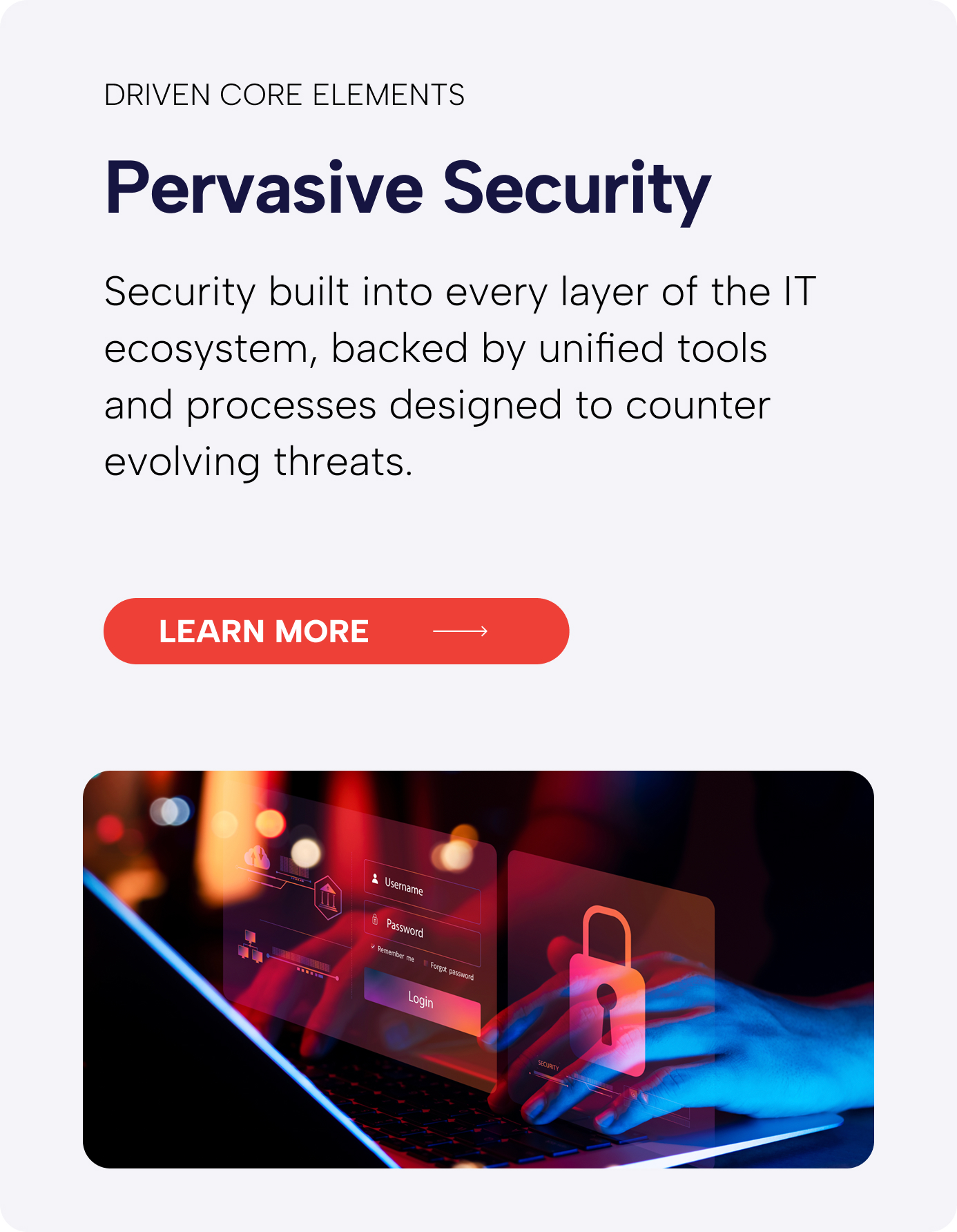
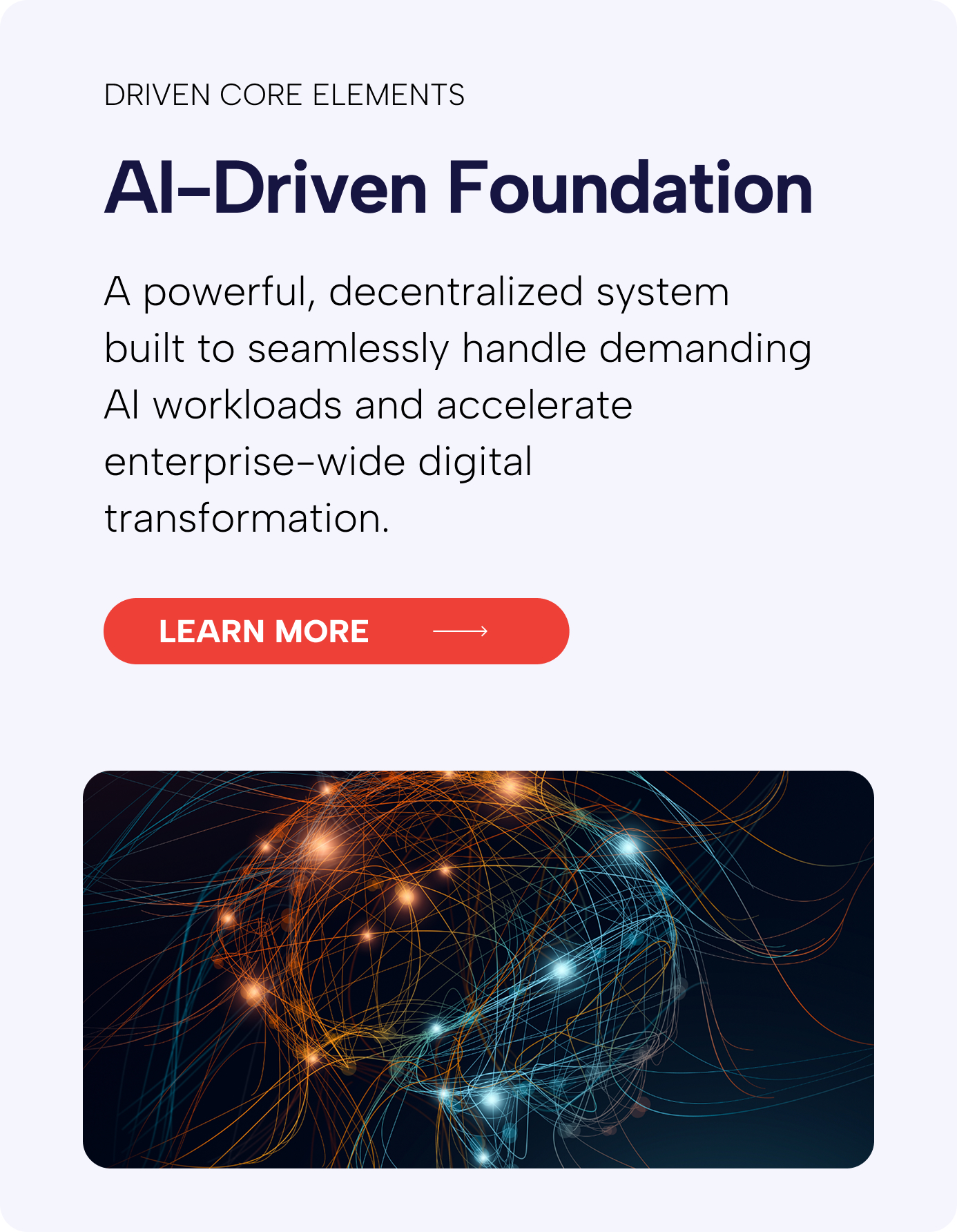
We think security every minute of every day so you don’t have to
Driven’s full range of services are tailored around your needs, not the other way around
True customized security
In today’s environment, no matter what industry you work in or how centralized or dispersed your workforce is, nothing is more important than ensuring that the security of your IT environment is constant and reliable. Even the smallest vulnerability can bring business as you and your company know it to a halt.
Driven’s ARMOR™-powered security services are designed to help predict, detect, and mitigate existing and emerging threats. Each of our solutions is tailored around your business needs and the structure of your company to make sure that you are protected both for today and tomorrow.
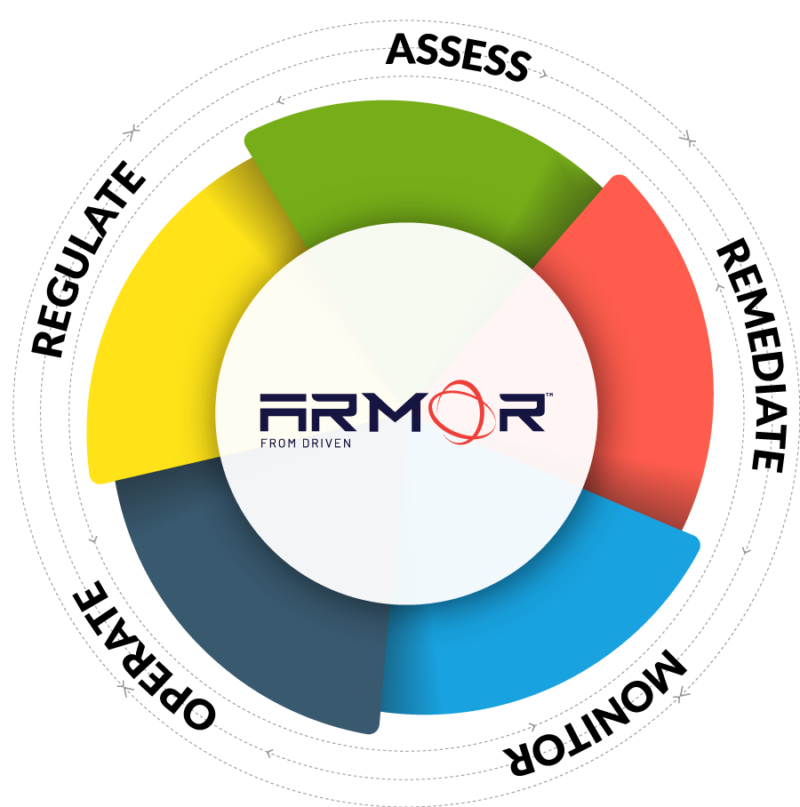
What we deliver to each of our clients from onboarding to fully operationalized.
We assess and protect all business assets by identifying threats, resolving incidents with full context, and hardening environments—while automating repetitive tasks to ensure continuous, efficient defense.
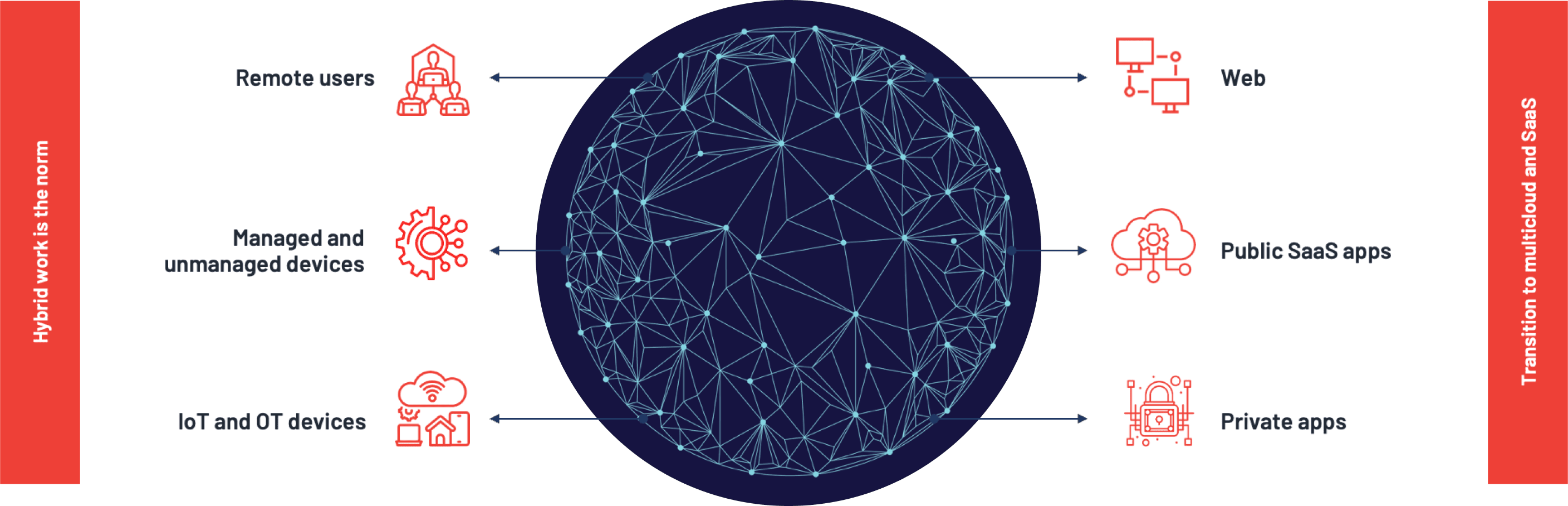
Today’s IT landscape is more distributed than ever
Hybrid work distributes users and devices across multiple locations. Their apps and workloads are also distributed across multiple locations: public internet, multi-cloud IaaS, data centers, etc.

Facets of complexity on the client end can be the enemy of security and speed
IT Teams are tasked to protect their organizations in the face of this complexity. However, there are many reasons why enterprises have slow threat responses.
Mediocre threat intelligence
Complex and fragmented architecture
Multi-step critical firmware updates
Human error and skills shortage
Security engineering: Defense in depth
- 1
Security awareness training and phishing campaigns
- 2
Network security (URL filtering, SSL decryption, etc.)
- 3
EDR (Endpoint Detect and Response)
- 4
Perimeter (north-south) and internal (east-west) firewalls
- 5
CNAPP (Cloud Native Application Protection Platform)
- 6
ASM (Attack Surface Management)
- 7Vulnerability and patch management
- 8IAM (Identity Access Management)
- 9
Sensitive data (pi, phi, cardholder data, “crown jewels”)