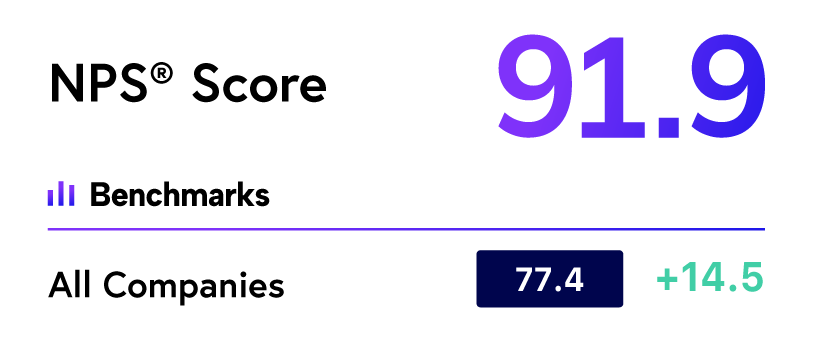
Relentless Threat Hunting
Driven AI/human threat hunting process provides peace-of-mind to focus on business growth
Dynamic AI capabilities meet human experience
Driven’s processes are a unique combination of AI technology and human experience provides a dynamic and predictive wall of security.
Our innovative redefinition of processes and threat detection rules is based on potential deviations on threat hunting findings.
Adjusted security architecture is deployed based on a combination of threat hunting findings and potential vulnerabilities related to existing system weaknesses and exposure.
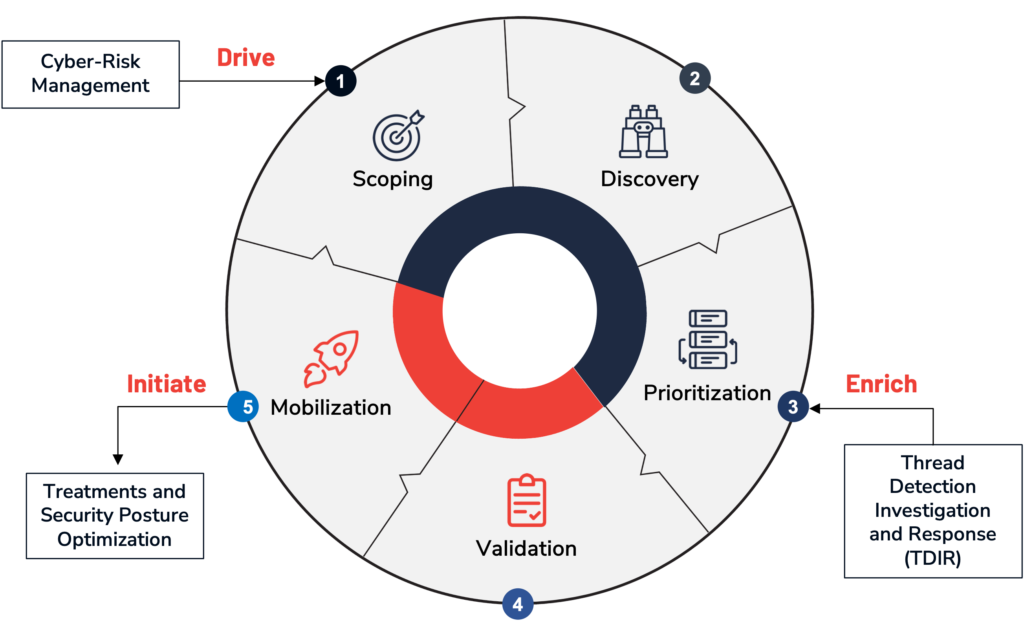
Continuous threat exposure management (CTM)
A pragmatic and systemic approach to continuously adjust cybersecurity optimization priorities
Build and protect your organization while generating value
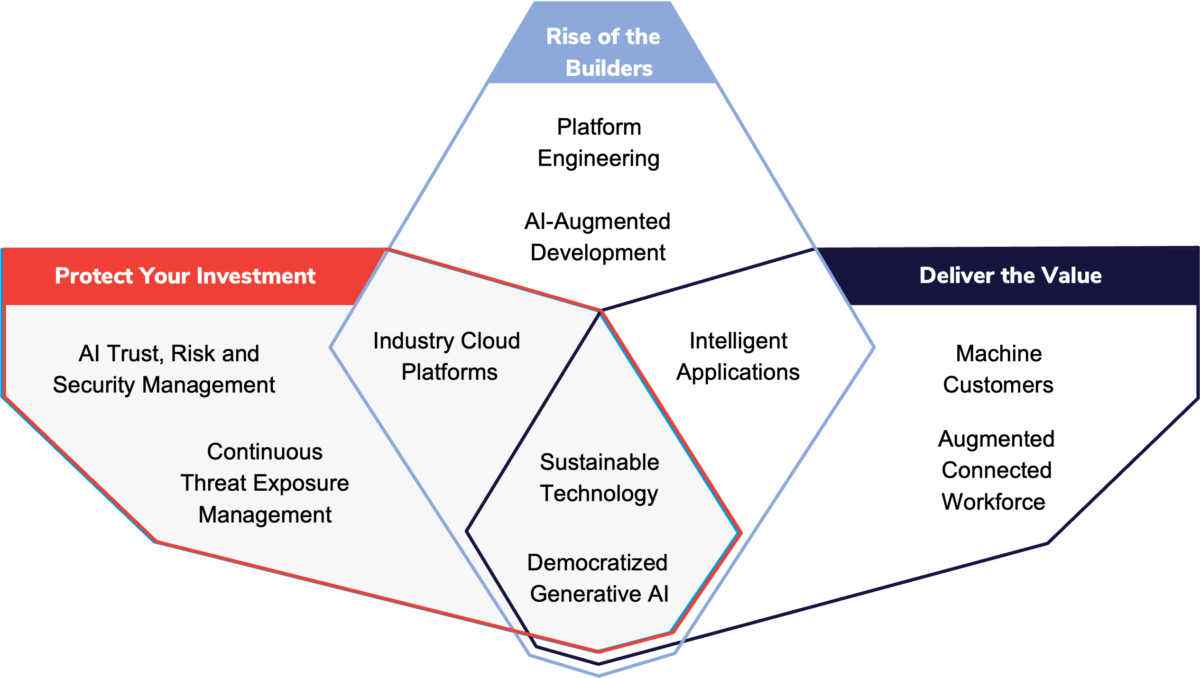
Gartner expects these 10 trends — which each fall into one or more categories — to factor into many business and technology decisions over the next 36 months. Your business goals will determine which you plan to leverage, and when.