Flipping the traditional approach for better outcomes
Finding the right mix of modernization is key to keeping ahead of threats without overwhelming existing resources and teams
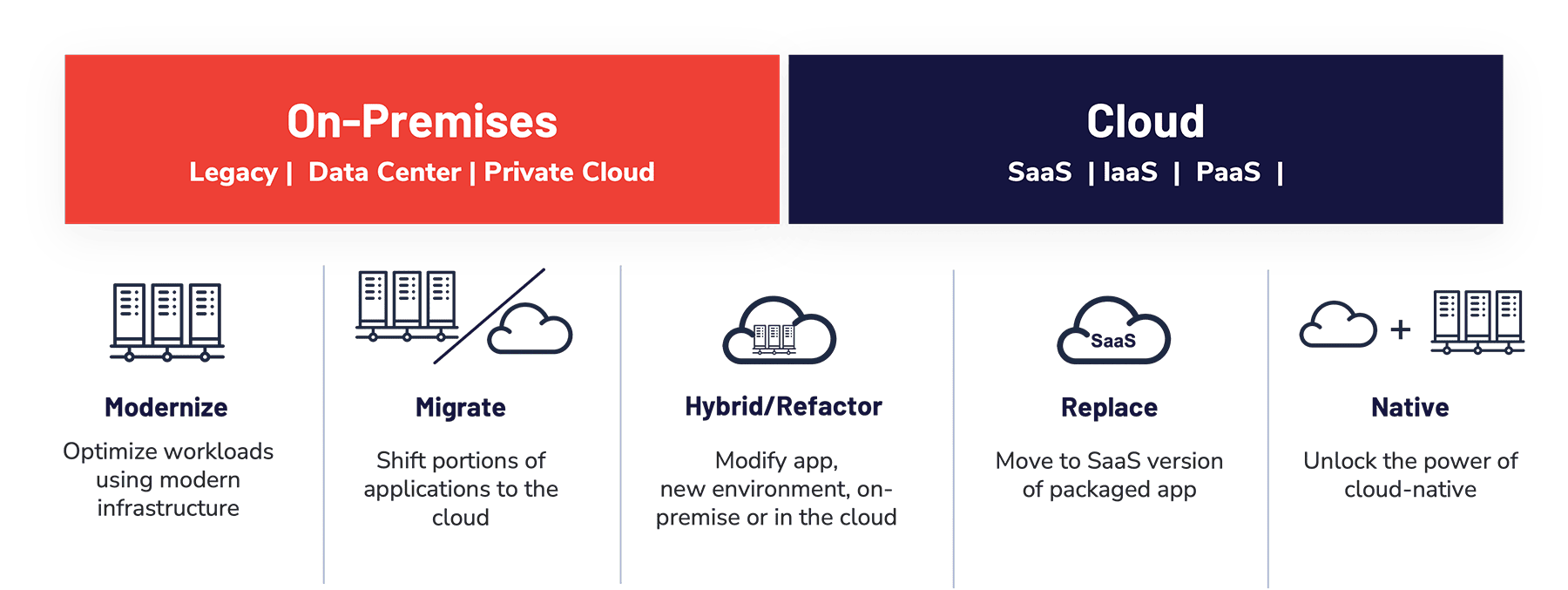
Systems modernization relies on an applications-down approach
Our modernization strategy starts with an Applications-Down approach. Unlike traditional VARs, which look at the infrastructure first, we look at the applications and then evaluate the best modernization approach with our patent pending AXIOM™ framework.
$300B
global spending on AI by 2026
82%
of businesses say their network environment is more complex than it was two years ago.
Critical modernization keypoints
Companies can effectively combat behavior-based threats using advanced technologies such as machine learning for anomaly detection and real-time monitoring. These technologies enable proactive identification of suspicious activities and deviations from normal behavior patterns. By leveraging these tools, organizations can strengthen their defenses against evolving threats posed by malicious actors.

Enterprise Networks & Security
Network is a commodity. We differentiate with security, application visibility, and operational simplicity solutions.
Cyberattack possibilities are endless. We lead with a cohesive security strategy, not point product solutions.
- NAC
- NG Firewalls and Endpoints
- SD-WAN
- SASE
- Wireless & Mobility

Collaboration & Internet of Things (IOT)
Greenfield UC deployments are rare. We deliver enhancements to our customer’s UC, Video, and Cloud Contact Center environments.
IoT is a growing area of opportunity. We engage the LOB decision makers.
- Unified Communications
- Web Conferencing
- AV Office Space Design
- Contact Centers

Data Centers
Data Centers are shifting from network-centric to application-centric. We specialize in “Zero Trust” data center security and application dependency mapping tools.
We differentiate with our service provider experience.
- Compute & Storage
- Backup & Recovery
- Hyperconverged
- SDDC and DC Switching
- Multi-Cloud Deployments
Our SOC, an extension of your team
We focus on more than just safeguarding your business from threats. We work closely with your team to advance your overall security posture, which at its core requires clear and collaborative communication.
Our communication is structured to match yours, including key metric reviews, regular cadence meetings, needs assessments, and more. Guided by Quarterly Business Reviews, we will establish performance standards, KPI expectations, and financial parameters with you, as well as set future goals and objectives.
EVERY cloud journey is different. Workloads are at the center of our cloud methodology.